CAS-003 문제 551
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary data.
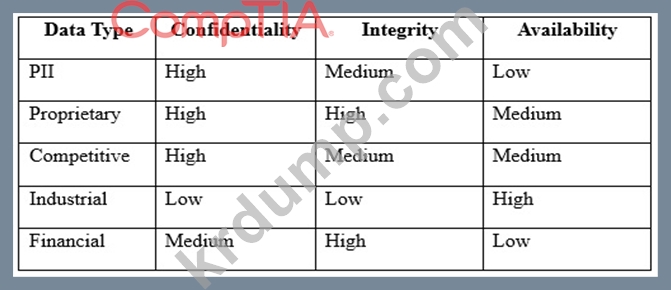
Based on the data classification table above, which of the following BEST describes the overall classification?

Based on the data classification table above, which of the following BEST describes the overall classification?
CAS-003 문제 552
A security analyst is reviewing the security of a company's public-facing servers After some research the analyst discovers the following on a public pastebin website.
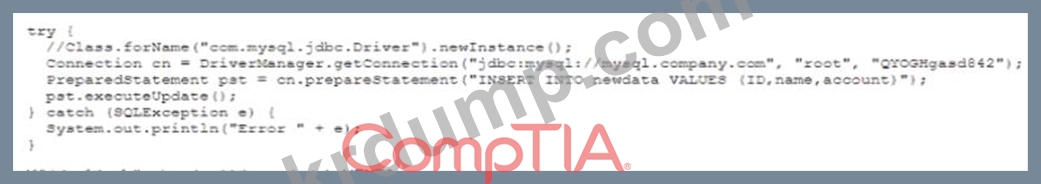
Which of the following should the analyst do NEXT?

Which of the following should the analyst do NEXT?
CAS-003 문제 553
Customers are receiving emails containing a link to malicious software. These emails are subverting spam filters. The email reads as follows:
Delivered-To: [email protected]
Received: by 10.14.120.205
Mon, 1 Nov 2010 11:15:24 -0700 (PDT)
Received: by 10.231.31.193
Mon, 01 Nov 2010 11:15:23 -0700 (PDT)
Return-Path: <[email protected]>
Received: from 127.0.0.1 for <[email protected]>; Mon, 1 Nov 2010
13:15:14 -0500
(envelope-from <[email protected]>)
Received: by smtpex.example.com (SMTP READY)
with ESMTP (AIO); Mon, 01 Nov 2010 13:15:14 -0500
Received: from 172.18.45.122 by 192.168.2.55; Mon, 1 Nov 2010 13:15:14
-0500
From: Company <[email protected]>
To: "[email protected]" <[email protected]>
Date: Mon, 1 Nov 2010 13:15:11 -0500
Subject: New Insurance Application
Thread-Topic: New Insurance Application
Please download and install software from the site below to maintain
full access to your
account.
www.examplesite.com
________________________________
Additional information: The authorized mail servers IPs are
192.168.2.10 and 192.168.2.11.
The network's subnet is 192.168.2.0/25.
Which of the following are the MOST appropriate courses of action a security administrator could take to eliminate this risk? (Select TWO).
Delivered-To: [email protected]
Received: by 10.14.120.205
Mon, 1 Nov 2010 11:15:24 -0700 (PDT)
Received: by 10.231.31.193
Mon, 01 Nov 2010 11:15:23 -0700 (PDT)
Return-Path: <[email protected]>
Received: from 127.0.0.1 for <[email protected]>; Mon, 1 Nov 2010
13:15:14 -0500
(envelope-from <[email protected]>)
Received: by smtpex.example.com (SMTP READY)
with ESMTP (AIO); Mon, 01 Nov 2010 13:15:14 -0500
Received: from 172.18.45.122 by 192.168.2.55; Mon, 1 Nov 2010 13:15:14
-0500
From: Company <[email protected]>
To: "[email protected]" <[email protected]>
Date: Mon, 1 Nov 2010 13:15:11 -0500
Subject: New Insurance Application
Thread-Topic: New Insurance Application
Please download and install software from the site below to maintain
full access to your
account.
www.examplesite.com
________________________________
Additional information: The authorized mail servers IPs are
192.168.2.10 and 192.168.2.11.
The network's subnet is 192.168.2.0/25.
Which of the following are the MOST appropriate courses of action a security administrator could take to eliminate this risk? (Select TWO).
CAS-003 문제 554
Designing a system in which only information that is essential for a particular job task is allowed to be viewed can be accomplished successfully by using:
CAS-003 문제 555
A software development manager is running a project using agile development methods.
The company cybersecurity engineer has noticed a high number of vulnerabilities have been making it into production code on the project.
Which of the following methods could be used in addition to an integrated development environment to reduce the severity of the issue?
The company cybersecurity engineer has noticed a high number of vulnerabilities have been making it into production code on the project.
Which of the following methods could be used in addition to an integrated development environment to reduce the severity of the issue?

