CAS-003 문제 571
A technician receives the following security alert from the firewall's automated system:
Match_Time: 10/10/16 16:20:43
Serial: 002301028176
Device_name: COMPSEC1
Type: CORRELATION
Scrusex: domain\samjones
Scr: 10.50.50.150
Object_name: beacon detection
Object_id: 6005
Category: compromised-host
Severity: medium
Evidence: host repeatedly visited a dynamic DNS domain (17 time)
After reviewing the alert, which of the following is the BEST analysis?
Match_Time: 10/10/16 16:20:43
Serial: 002301028176
Device_name: COMPSEC1
Type: CORRELATION
Scrusex: domain\samjones
Scr: 10.50.50.150
Object_name: beacon detection
Object_id: 6005
Category: compromised-host
Severity: medium
Evidence: host repeatedly visited a dynamic DNS domain (17 time)
After reviewing the alert, which of the following is the BEST analysis?
CAS-003 문제 572
A company has entered into a business agreement with a business partner for managed human resources services. The Chief Information Security Officer (CISO) has been asked to provide documentation that is required to set up a business-to-business VPN between the two organizations.
Which of the following is required in this scenario?
Which of the following is required in this scenario?
CAS-003 문제 573
A software company is releasing a new mobile application to a broad set of external customers. Because the software company is rapidly releasing new features, it has built in an over-the-air software update process that can automatically update the application at launch time. Which of the following security controls should be recommended by the company's security architect to protect the integrity of the update process? (Choose two.)
CAS-003 문제 574
A multi-national company has a highly mobile workforce and minimal IT infrastructure. The company utilizes a BYOD and social media policy to integrate presence technology into global collaboration tools by individuals and teams. As a result of the dispersed employees and frequent international travel, thecompany is concerned about the safety of employees and their families when moving in and out of certain countries.
Which of the following could the company view as a downside of using presence technology?
Which of the following could the company view as a downside of using presence technology?
CAS-003 문제 575
When reviewing KRIs of the email security appliance with the Chief Information Security Officer (CISO) of an insurance company, the security engineer notices the following:
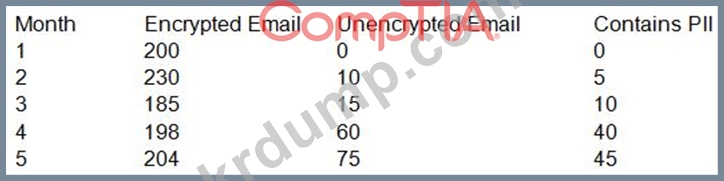
Which of the following measures should the security engineer take to ensure PII is not intercepted in transit while also preventing interruption to business?

Which of the following measures should the security engineer take to ensure PII is not intercepted in transit while also preventing interruption to business?

