CAS-003 문제 526
A penetration tester is conducting an assessment on Comptia.org and runs the following command from a coffee shop while connected to the public Internet:
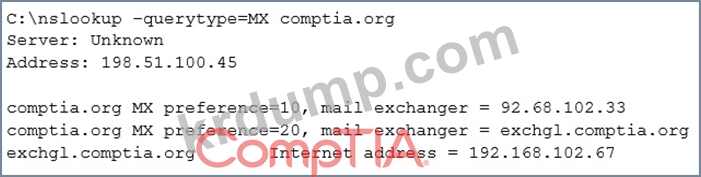
Which of the following should the penetration tester conclude about the command output?

Which of the following should the penetration tester conclude about the command output?
CAS-003 문제 527
A security architect is implementing security measures in response to an external audit that found vulnerabilities in the corporate collaboration tool suite. The report identified the lack of any mechanism to provide confidentiality for electronic correspondence between users and between users and group mailboxes. Which of the following controls would BEST mitigate the identified vulnerability?
CAS-003 문제 528
While attending a meeting with the human resources department, an organization's information security officer sees an employee using a username and password written on a memo pad to log into a specific service. When the information security officer inquires further as to why passwords are being written down, the response is that there are too many passwords to remember for all the different services the human resources department is required to use.
Additionally, each password has specific complexity requirements and different expiration time frames. Which of the following would be the BEST solution for the information security officer to recommend?
Additionally, each password has specific complexity requirements and different expiration time frames. Which of the following would be the BEST solution for the information security officer to recommend?
CAS-003 문제 529
As part of incident response, a technician is taking an image of a compromised system and copying the image to a remote image server (192.168.45.82). The system drive is very large but does not contain the sensitive data. The technician has limited time to complete this task. Which of the following is the BEST command for the technician to run?
CAS-003 문제 530
해커인 Joe는 브라우저에서 볼 때 브라우저가 충돌하고 피해자의 권한 수준 컨텍스트에서 원격 코드 실행을 얻을 수 있는 웹 페이지를 특별히 제작할 수 있다는 것을 발견했습니다. 사용하지 않는 힙 메모리에 접근할 때 예외 오류로 인해 브라우저가 충돌합니다. 다음 중 애플리케이션 문제를 가장 잘 설명한 것은 무엇입니까?

