CAS-003 문제 556
An enterprise with global sites processes and exchanges highly sensitive information that is protected under several countries' arms trafficking laws. There is new information that malicious nation-state-sponsored activities are targeting the use of encryption between the geographically disparate sites. The organization currently employs ECDSA and ECDH with P-384, SHA-384, and AES-256-GCM on VPNs between sites. Which of the following techniques would MOST likely improve the resilience of the enterprise to attack on cryptographic implementation?
CAS-003 문제 557
Following a recent outage a systems administrator is conducting a study to determine a suitable bench stock of server hard drives. Which of the following metrics is MOST valuable to the administrator in determining how many hard drives to keep on hand?
CAS-003 문제 558
A security engineer successfully exploits an application during a penetration test. As proof of the exploit, the security engineer takes screenshots of how data was compromised in the application. Given the information below from the screenshot.
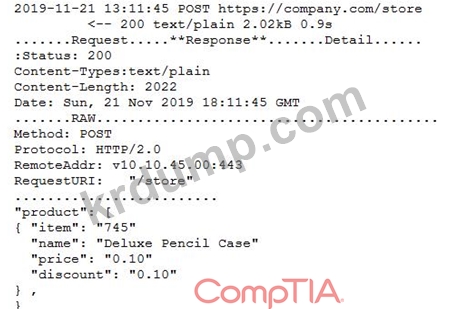
Which of the following tools was MOST likely used to exploit the application?

Which of the following tools was MOST likely used to exploit the application?
CAS-003 문제 559
A company contracts a security engineer to perform a penetration test of its client-facing web portal. Which
of the following activities would be MOST appropriate?
of the following activities would be MOST appropriate?
CAS-003 문제 560
보안 제어 평가자는 네트워크로 연결된 전체적 구성 준수 테스트를 수행하려고 합니다.
자산. 평가자는 XML 형식으로 제공되는 정의 패키지를 받았으며 많은
파일에는 "<object object_ref=... />" 및 "<state state_ref=...라는 두 개의 공통 태그가 있습니다.
/>".다음 도구 중 이러한 정의의 사용을 가장 잘 지원하는 도구는 무엇입니까?
자산. 평가자는 XML 형식으로 제공되는 정의 패키지를 받았으며 많은
파일에는 "<object object_ref=... />" 및 "<state state_ref=...라는 두 개의 공통 태그가 있습니다.
/>".다음 도구 중 이러한 정의의 사용을 가장 잘 지원하는 도구는 무엇입니까?

