CAS-003 문제 391
A security consultant is conducting a network assessment and wishes to discover any legacy backup Internet connections the network may have. Where would the consultant find this information and why would it be valuable?
CAS-003 문제 392
A breach was caused by an insider threat in which customer PII was compromised. Following the breach, a lead security analyst is asked to determine which vulnerabilities the attacker used to access company resources.
Which of the following should the analyst use to remediate the vulnerabilities?
Which of the following should the analyst use to remediate the vulnerabilities?
CAS-003 문제 393
A security consultant is considering authentication options for a financial institution. The following authentication options are available. Drag and drop the security mechanism to the appropriate use case. Options may be used once.


CAS-003 문제 394
A software company is releasing a new mobile application to a broad set of external customers. Because the software company is rapidly releasing new features, it has built in an over-the-air software update process that can automatically update the application at launch time. Which of the following security controls should be recommended by the company's security architect to protect the integrity of the update process? (Choose two.)
CAS-003 문제 395
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary
data.
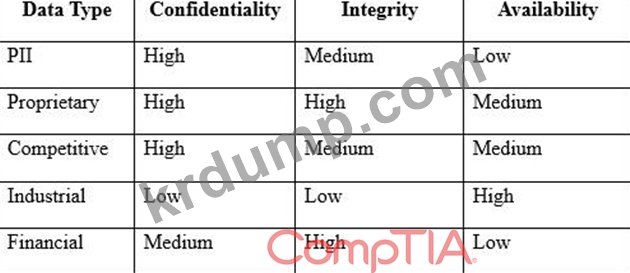
Based on the data classification table above, which of the following BEST describes the overall
classification?
data.

Based on the data classification table above, which of the following BEST describes the overall
classification?


