CAS-003 문제 386
A company has decided to lower costs by conducting an internal assessment on specific devices and
various internal and external subnets. The assessment will be done during regular office hours, but it must
not affect any production servers.
Which of the following would MOST likely be used to complete the assessment? (Select two.)
various internal and external subnets. The assessment will be done during regular office hours, but it must
not affect any production servers.
Which of the following would MOST likely be used to complete the assessment? (Select two.)
CAS-003 문제 387
A company uses an application in its warehouse that works with several commercially available tablets and can only be accessed inside the warehouse. The support department would like the selection of tablets to be limited to three models to provide better support and ensure spares are on hand. Users often keep the tablets after they leave the department, as many of them store personal media items.
Which of the following should the security engineer recommend to meet these requirements?
Which of the following should the security engineer recommend to meet these requirements?
CAS-003 문제 388
An information security officer reviews a report and notices a steady increase in outbound network traffic over the past ten months. There is no clear for the increase The security officer interviews several business units and discovers an unsanctioned cloud storage provider was used to share marketing materials with potential customers. Which of the following services would be BEST for the security officer to recommend to the company?
CAS-003 문제 389
A new security policy slates all wireless and wired authentication must include the use of certificates when connecting to internal resources within the enterprise LAN by all employees Which of the following should be configured to comply with the new security policy? (Select TWO).
CAS-003 문제 390
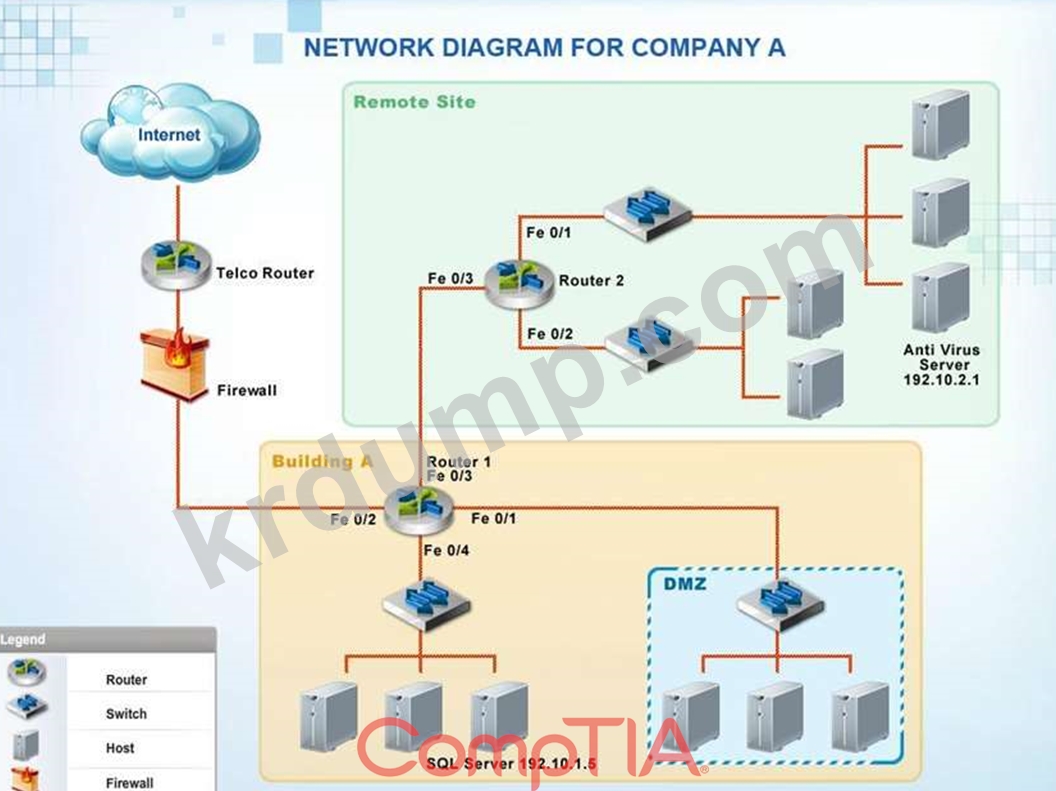
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP address.
The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and
192.10.2.0/24 for the remote site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
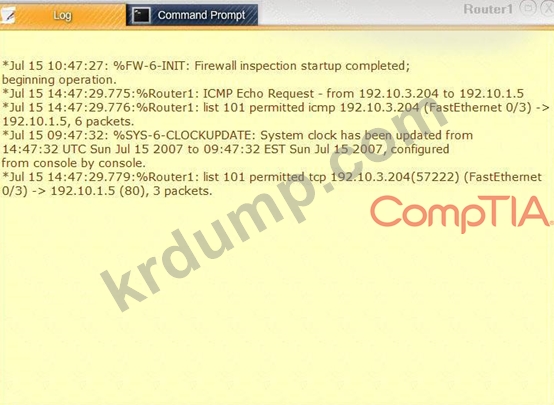
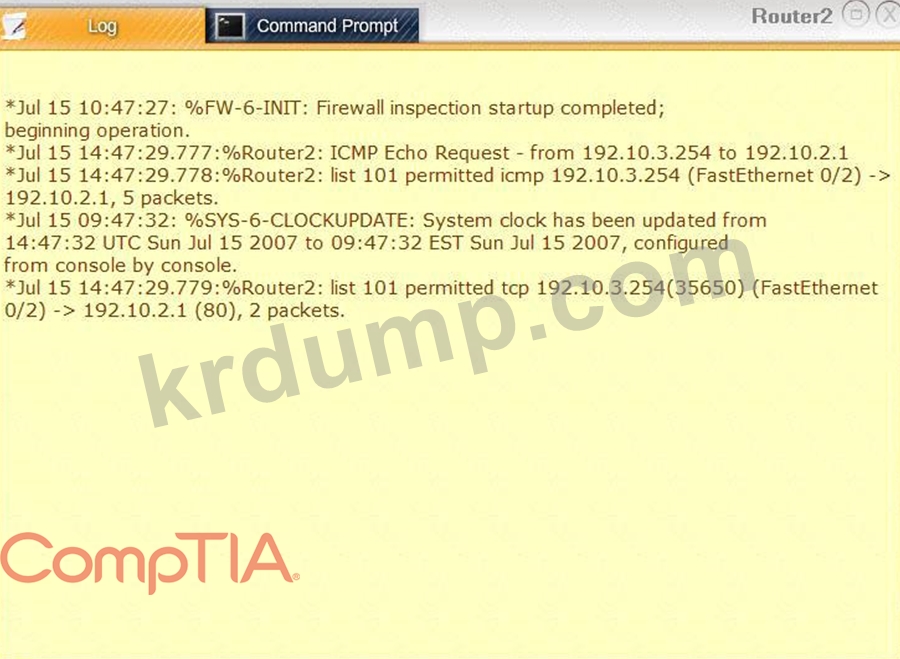
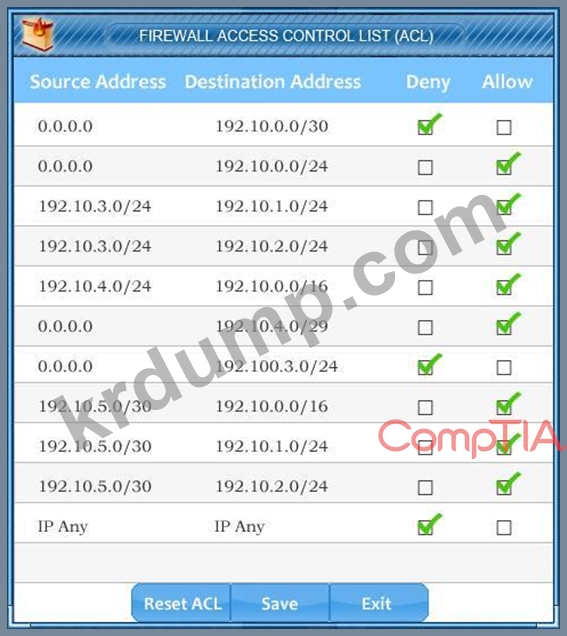
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.
The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and
192.10.2.0/24 for the remote site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.





