CAS-003 문제 506
At 9:00 am each morning, all of the virtual desktops in a VDI implementation become extremely slow and/or unresponsive. The outage lasts for around 10 minutes, after which everything runs properly again. The administrator has traced the problem to a lab of thin clients that are all booted at 9:00 am each morning. Which of the following is the MOST likely cause of the problem and the BEST solution? (Select TWO).
CAS-003 문제 507
A penetration tester is inspecting traffic on a new mobile banking application and sends the following web request:
POST http://www.example.com/resources/NewBankAccount HTTP/1.1
Content-type: application/json
{
"account":
[
{ "creditAccount":"Credit Card Rewards account"}
{ "salesLeadRef":"www.example.com/badcontent/exploitme.exe"}
],
"customer":
[
{ "name":"Joe Citizen"}
{ "custRef":"3153151"}
]
}
The banking website responds with:
HTTP/1.1 200 OK
{
"newAccountDetails":
[
{ "cardNumber":"1234123412341234"}
{ "cardExpiry":"2020-12-31"}
{ "cardCVV":"909"}
],
"marketingCookieTracker":"JSESSIONID=000000001"
"returnCode":"Account added successfully"
}
Which of the following are security weaknesses in this example? (Select TWO).
POST http://www.example.com/resources/NewBankAccount HTTP/1.1
Content-type: application/json
{
"account":
[
{ "creditAccount":"Credit Card Rewards account"}
{ "salesLeadRef":"www.example.com/badcontent/exploitme.exe"}
],
"customer":
[
{ "name":"Joe Citizen"}
{ "custRef":"3153151"}
]
}
The banking website responds with:
HTTP/1.1 200 OK
{
"newAccountDetails":
[
{ "cardNumber":"1234123412341234"}
{ "cardExpiry":"2020-12-31"}
{ "cardCVV":"909"}
],
"marketingCookieTracker":"JSESSIONID=000000001"
"returnCode":"Account added successfully"
}
Which of the following are security weaknesses in this example? (Select TWO).
CAS-003 문제 508
The government is concerned with remote military missions being negatively impacted by the use of technology that may fail to protect operational security. To remediate this concern, a number of solutions have been implemented, including the following:
* End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that allow solders to securely communicate with families
* Layer 7 inspection and TCP/UDP port restriction, including firewall rules to only allow TCP port 80 and 443 and approved applications
* A host-based whitelist of approved websites and applications that only allow mission-related tools and sites
* The use of satellite communication to include multiple proxy servers to scramble the source IP address Which of the following is of MOST concern in this scenario?
* End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that allow solders to securely communicate with families
* Layer 7 inspection and TCP/UDP port restriction, including firewall rules to only allow TCP port 80 and 443 and approved applications
* A host-based whitelist of approved websites and applications that only allow mission-related tools and sites
* The use of satellite communication to include multiple proxy servers to scramble the source IP address Which of the following is of MOST concern in this scenario?
CAS-003 문제 509
새 회계 PC용 원본 워크스테이션 이미지가 블루스크린을 시작했습니다. 기술자는 이미지 소스의 날짜/시간 스탬프가 변경된 것으로 보입니다.
데스크탑 지원 이사는 정보 보안 부서에 원본 이미지에 변경 사항이 있는지 확인하도록 요청했습니다. 다음 중 이 프로세스에 가장 도움이 되는 방법은 무엇입니까? (2개 선택).
데스크탑 지원 이사는 정보 보안 부서에 원본 이미지에 변경 사항이 있는지 확인하도록 요청했습니다. 다음 중 이 프로세스에 가장 도움이 되는 방법은 무엇입니까? (2개 선택).
CAS-003 문제 510
Compliance with company policy requires a quarterly review of firewall rules. You are asked to conduct a review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more secure. Given the following information perform the tasks listed below:
Untrusted zone: 0.0.0.0/0
User zone: USR 10.1.1.0/24
User zone: USR2 10.1.2.0/24
DB zone: 10.1.4.0/24
Web application zone: 10.1.5.0/24
Management zone: 10.1.10.0/24
Web server: 10.1.5.50
MS-SQL server: 10.1.4.70
MGMT platform: 10.1.10.250
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
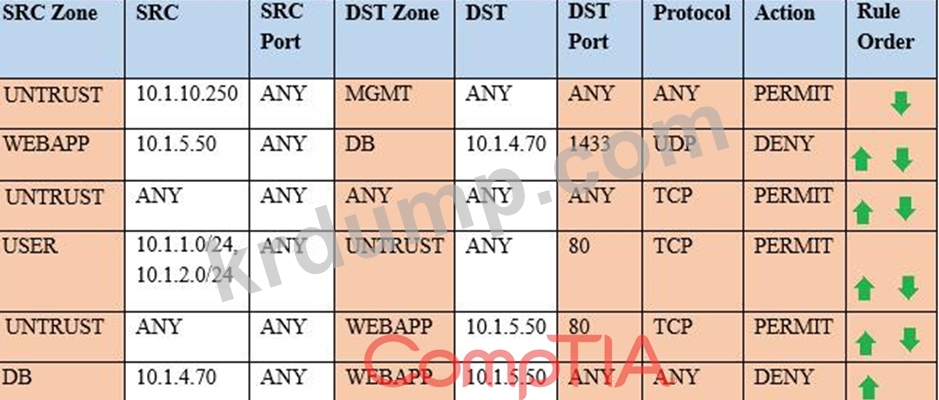
Task 1) A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
Task 2) The firewall must be configured so that the SQL server can only receive requests from the web server.
Task 3) The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network.
Task 4) Ensure the final rule is an explicit deny.
Task 5) Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only.
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Untrusted zone: 0.0.0.0/0
User zone: USR 10.1.1.0/24
User zone: USR2 10.1.2.0/24
DB zone: 10.1.4.0/24
Web application zone: 10.1.5.0/24
Management zone: 10.1.10.0/24
Web server: 10.1.5.50
MS-SQL server: 10.1.4.70
MGMT platform: 10.1.10.250
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

Task 1) A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
Task 2) The firewall must be configured so that the SQL server can only receive requests from the web server.
Task 3) The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network.
Task 4) Ensure the final rule is an explicit deny.
Task 5) Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only.
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

