CAS-003 문제 491
An online bank has contracted with a consultant to perform a security assessment of the bank's web portal.
The consultant notices the login page is linked from the main page with HTTPS, but when the URL is changed to HTTP, the browser is automatically redirected back to the HTTPS site. Which of the following is a concern for the consultant, and how can it be mitigated?
The consultant notices the login page is linked from the main page with HTTPS, but when the URL is changed to HTTP, the browser is automatically redirected back to the HTTPS site. Which of the following is a concern for the consultant, and how can it be mitigated?
CAS-003 문제 492
Which of the following BEST represents a risk associated with merging two enterprises during an acquisition?
CAS-003 문제 493
A company is implementing a new secure identity application, given the following requirements
* The cryptographic secrets used in the application must never be exposed to users or the OS
* The application must work on mobile devices.
* The application must work with the company's badge reader system
Which of the following mobile device specifications are required for this design? (Select TWO).
* The cryptographic secrets used in the application must never be exposed to users or the OS
* The application must work on mobile devices.
* The application must work with the company's badge reader system
Which of the following mobile device specifications are required for this design? (Select TWO).
CAS-003 문제 494
A company is migrating systems from an on-premises facility to a third-party managed datacenter. For continuity of operations and business agility, remote access to all hardware platforms must be available at all times. Access controls need to be very robust and provide an audit trail. Which of the following security controls will meet the company's objectives? (Choose two.)
CAS-003 문제 495
보안 엔지니어는 개별 엔드포인트의 고유한 구성과 공통 장치의 공유 구성 정책에 적용되는 회사 보안 정책의 준수 여부를 평가하는 방법을 수립해야 합니다.
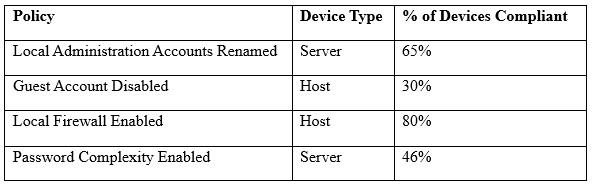
다음 중 보안 엔지니어가 위의 결과를 생성하는 데 사용하는 도구는 무엇입니까?

다음 중 보안 엔지니어가 위의 결과를 생성하는 데 사용하는 도구는 무엇입니까?

