CAS-003 문제 421
At a meeting, the systems administrator states the security controls a company wishes to implement seem excessive, since all of the information on the company's web servers can be obtained publicly and is not proprietary in any way. The next day the company's website is defaced as part of an SQL injection attack, and the company receives press inquiries about the message the attackers displayed on the website.
Which of the following is the FIRST action the company should take?
Which of the following is the FIRST action the company should take?
CAS-003 문제 422
The code snippet below controls all electronic door locks to a secure facility in which the doors should only fail open in an emergency. In the code, "criticalValue" indicates if an emergency is underway:
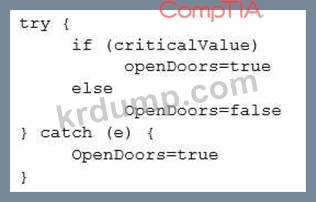
Which of the following is the BEST course of action for a security analyst to recommend to the software developer?

Which of the following is the BEST course of action for a security analyst to recommend to the software developer?
CAS-003 문제 423
Several recent ransomware outbreaks at a company have cost a significant amount of lost revenue. The security team needs to find a technical control mechanism that will meet the following requirements and aid in preventing these outbreaks:
* Stop malicious software that does not match a signature
* Report on instances of suspicious behavior
* Protect from previously unknown threats
* Augment existing security capabilities
Which of the following tools would BEST meet these requirements?
* Stop malicious software that does not match a signature
* Report on instances of suspicious behavior
* Protect from previously unknown threats
* Augment existing security capabilities
Which of the following tools would BEST meet these requirements?
CAS-003 문제 424
A penetration tester is conducting an assessment on Comptia.org and runs the following command from a coffee shop while connected to the public Internet:
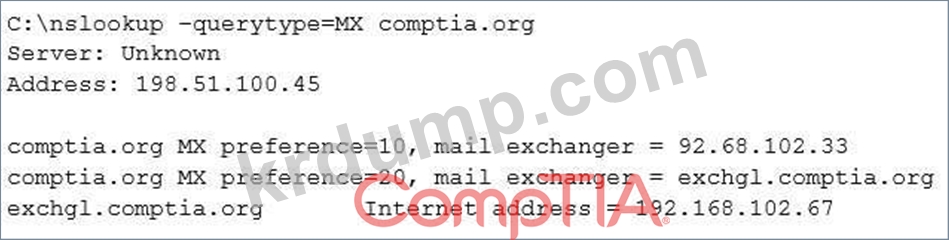
Which of the following should the penetration tester conclude about the command output?

Which of the following should the penetration tester conclude about the command output?
CAS-003 문제 425
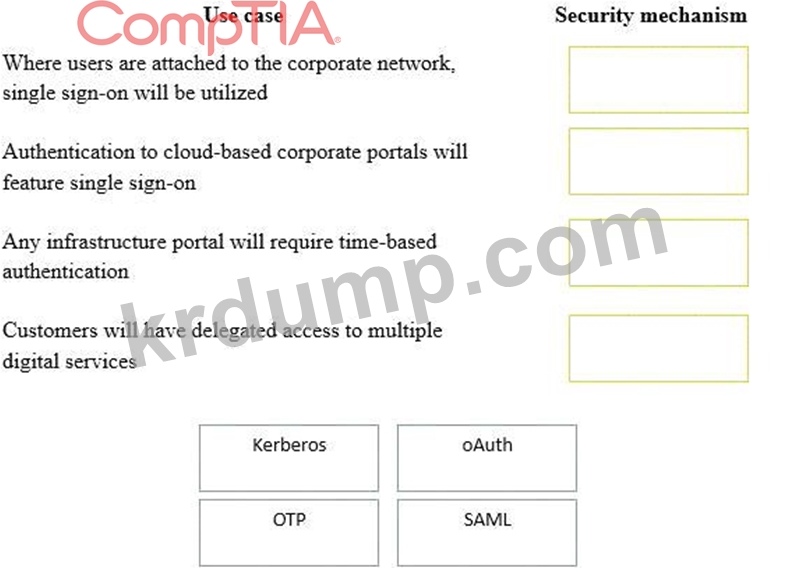
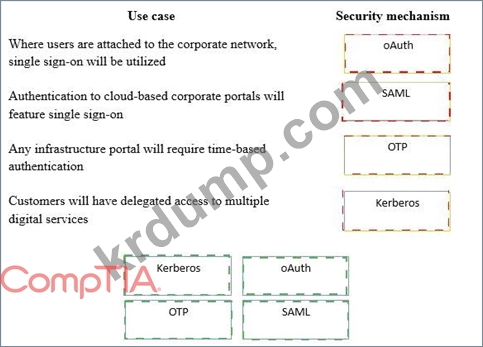
A security consultant is considering authentication options for a financial institution. The following authentication options are available security mechanism to the appropriate use case. Options may be used once.