CAS-003 문제 326
A company's existing forward proxies support software-based TLS decryption, but are currently at 60% load just dealing with AV scanning and content analysis for HTTP traffic. More than 70% outbound web traffic is currently encrypted. The switching and routing network infrastructure precludes adding capacity, preventing the installation of a dedicated TLS decryption system. The network firewall infrastructure is currently at 30% load and has software decryption modules that can be activated by purchasing additional license keys. An existing project is rolling out agent updates to end-user desktops as part of an endpoint security refresh.
Which of the following is the BEST way to address these issues and mitigate risks to the organization?
Which of the following is the BEST way to address these issues and mitigate risks to the organization?
CAS-003 문제 327
An information security officer reviews a report and notices a steady increase in outbound network traffic over the past ten months. There is no clear explanation for the increase The security officer interviews several business units and discovers an unsanctioned cloud storage provider was used to share marketing materials with potential customers. Which of the following services would be BEST for the security officer to recommend to the company?
CAS-003 문제 328
During a security assessment, activities were divided into two phases; internal and external exploitation.
The security assessment team set a hard time limit on external activities before moving to a compromised box within the enterprise perimeter.
Which of the following methods is the assessment team most likely to employ NEXT?
The security assessment team set a hard time limit on external activities before moving to a compromised box within the enterprise perimeter.
Which of the following methods is the assessment team most likely to employ NEXT?
CAS-003 문제 329
보안 컨설턴트가 로컬 호스트와 클라우드 기반 서버로 구성된 로컬 엔터프라이즈 고객에 대한 침투 테스트를 수행하고 있습니다. 호스팅 서비스는 고객 요구를 충족하기 위해 탄력적인 프로비저닝이 포함된 다중 테넌트 모델을 사용합니다. 고객은 프로비저닝된 각 클라우드 호스트에서 여러 개의 가상화된 서버를 실행합니다. 보안 컨설턴트는 고객 네트워크에 침투하지 않고도 여러 세트의 관리자 자격 증명을 얻을 수 있습니다. 다음 중 테스터가 악용할 가능성이 가장 높은 위험은 무엇입니까?
CAS-003 문제 330
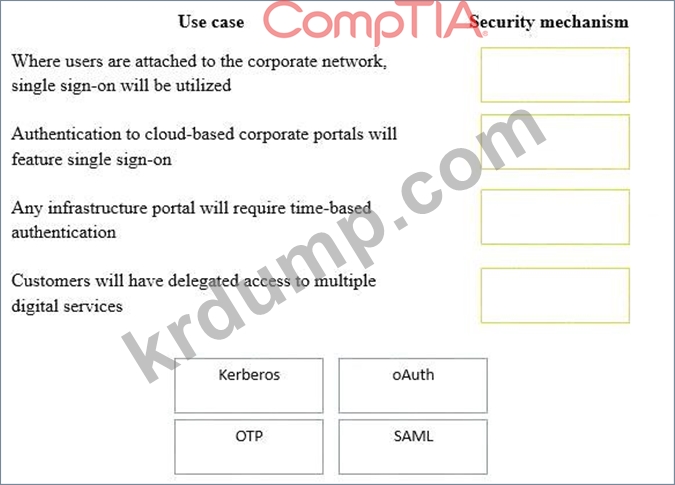
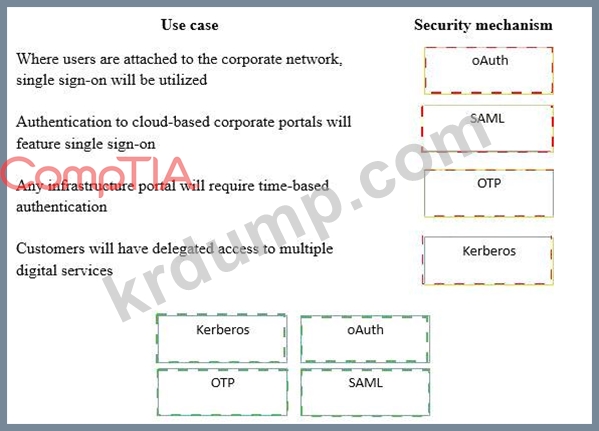
보안 컨설턴트가 금융 기관에 대한 인증 옵션을 고려하고 있습니다. 다음 인증 옵션은 적절한 사용 사례에 사용할 수 있는 보안 메커니즘입니다. 옵션은 한 번만 사용할 수 있습니다.