CAS-003 문제 316
A security technician receives a copy of a report that was originally sent to the board of directors by the Chief Information Security Officer (CISO).
The report outlines the following KPVKRI data for the last 12 months:
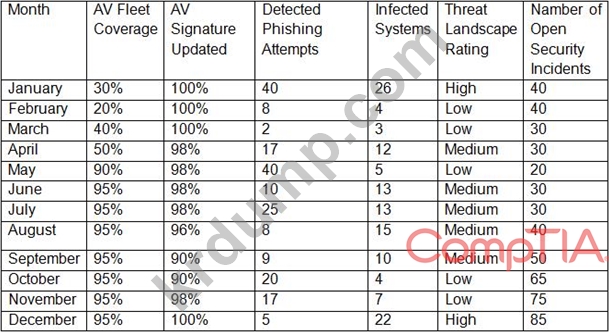
Which of the following BEST describes what could be interpreted from the above data?
The report outlines the following KPVKRI data for the last 12 months:

Which of the following BEST describes what could be interpreted from the above data?
CAS-003 문제 317
보안 관리자가 오프라인 암호 감사의 다음 출력을 검토하고 있습니다.
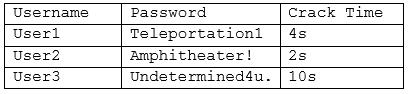
다음 중 시스템 관리자가 이 감사 결과를 가장 잘 처리하기 위해 구현해야 하는 것은 무엇입니까? (2개를 선택하세요.)

다음 중 시스템 관리자가 이 감사 결과를 가장 잘 처리하기 위해 구현해야 하는 것은 무엇입니까? (2개를 선택하세요.)
CAS-003 문제 318
A security engineer successfully exploits an application during a penetration test. As proof of the exploit, the security engineer takes screenshots of how data was compromised in the application. Given the information below from the screenshot.
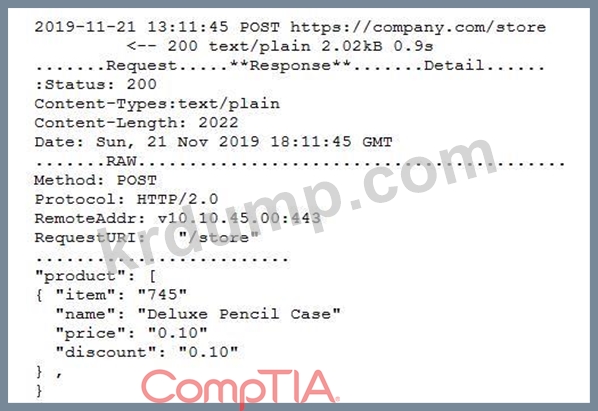
Which of the following tools was MOST likely used to exploit the application?

Which of the following tools was MOST likely used to exploit the application?
CAS-003 문제 319
A security analyst, who is working in a Windows environment, has noticed a significant amount of IPv6 traffic originating from a client, even though IPv6 is not currently in use. The client is a stand-alone device, not connected to the AD that manages a series of SCADA devices used for manufacturing. Which of the following is the appropriate command to disable the client's IPv6 stack?


CAS-003 문제 320
A large company with a very complex IT environment is considering a move from an on-premises, internally managed proxy to a cloud-based proxy solution managed by an external vendor. The current proxy provides caching, content filtering, malware analysis, and URL categorization for all staff connected behind the proxy.
Staff members connect directly to the Internet outside of the corporate network. The cloud-based version of the solution would provide content filtering, TLS decryption, malware analysis, and URL categorization. After migrating to the cloud solution, all internal proxies would be decommissioned. Which of the following would MOST likely change the company's risk profile?
Staff members connect directly to the Internet outside of the corporate network. The cloud-based version of the solution would provide content filtering, TLS decryption, malware analysis, and URL categorization. After migrating to the cloud solution, all internal proxies would be decommissioned. Which of the following would MOST likely change the company's risk profile?

