CAS-003 문제 221
A company monitors the performance of all web servers using WMI. A network administrator informs the security engineer that web servers hosting the company's client-facing portal are running slowly today. After some investigation, the security engineer notices a large number of attempts at enumerating host information via SNMP from multiple IP addresses.
Which of the following would be the BEST technique for the security engineer to employ in an attempt to prevent reconnaissance activity?
Which of the following would be the BEST technique for the security engineer to employ in an attempt to prevent reconnaissance activity?
CAS-003 문제 222
Given the following code snippet:
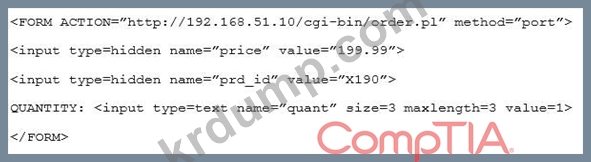
Of which of the following is this snippet an example?

Of which of the following is this snippet an example?
CAS-003 문제 223
A company is acquiring incident response and forensic assistance from a managed security service
provider in the event of a data breach. The company has selected a partner and must now provide
required documents to be reviewed and evaluated. Which of the following documents would BEST protect
the company and ensure timely assistance? (Choose two.)
provider in the event of a data breach. The company has selected a partner and must now provide
required documents to be reviewed and evaluated. Which of the following documents would BEST protect
the company and ensure timely assistance? (Choose two.)
CAS-003 문제 224
An infrastructure team is at the end of a procurement process and has selected a vendor. As part of the final negotiation, there are a number of outstanding issues, including:
1. Indemnity clauses have identified the maximum liability.
2. The data will be hosted and managed outside of the company's geographical location.
The number of users accessing the system will be small, and no sensitive data will be hosted in the solution. As the security consultant of the project, which of the following should the project's security consultant recommend as the NEXT step?
1. Indemnity clauses have identified the maximum liability.
2. The data will be hosted and managed outside of the company's geographical location.
The number of users accessing the system will be small, and no sensitive data will be hosted in the solution. As the security consultant of the project, which of the following should the project's security consultant recommend as the NEXT step?
CAS-003 문제 225
When generating a new key pair, a security application asks the user to move the mouse and type random characters on the keyboard.
Which of the following BEST describes why this is necessary?
Which of the following BEST describes why this is necessary?

