CAS-003 문제 216
내부 침투 테스터는 프로덕션 웹사이트로 푸시되기 전에 잠재적인 문제에 대한 채용 페이지를 평가하고 있었습니다. 침투 테스터는 페이지가 게시되기 전에 수정해야 하는 문제를 발견합니다. 웹 호스트 관리자는 아래의 로그 파일을 수집하여 웹 사이트의 보안 설계를 개선할 수 있도록 개발 팀에 제공합니다.
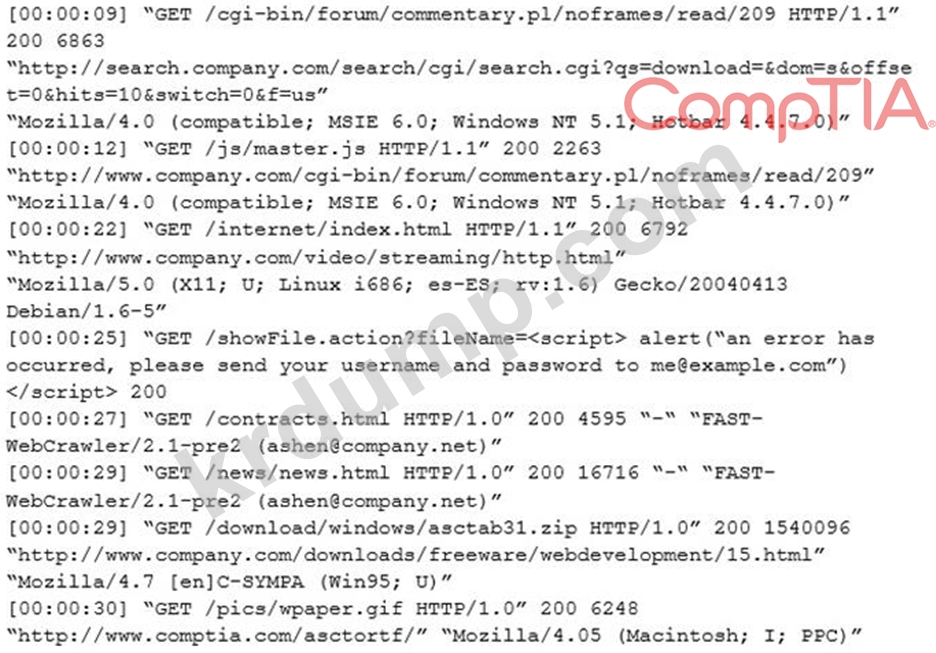
침투 테스터가 사용한 공격 벡터 유형은 다음 중 무엇입니까?

침투 테스터가 사용한 공격 벡터 유형은 다음 중 무엇입니까?
CAS-003 문제 217
A company has issued a new mobile device policy permitting BYOD and company-issued devices. The company-issued device has a managed middleware client that restricts the applications allowed on company devices and provides those that are approved. The middleware client provides configuration standardization for both company owned and BYOD to secure data and communication to the device according to industry best practices. The policy states that, "BYOD clients must meet the company's infrastructure requirements to permit a connection." The company also issues a memorandum separate from the policy, which provides instructions for the purchase, installation, and use of the middleware client on BYOD. Which of the following is being described?
CAS-003 문제 218
A system administrator has a responsibility to maintain the security of the video teleconferencing system.
During a self-audit of the video teleconferencing room, the administrator notices that speakers and microphones are hard-wired and wireless enabled.
Which of the following security concerns should the system administrator have about the existing technology in the room?
During a self-audit of the video teleconferencing room, the administrator notices that speakers and microphones are hard-wired and wireless enabled.
Which of the following security concerns should the system administrator have about the existing technology in the room?
CAS-003 문제 219
Compliance with company policy requires a quarterly review of firewall rules. A new administrator is asked to conduct this review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more restrictive. Given the following information answer the questions below:
User Subnet: 192.168.1.0/24 Server Subnet: 192.168.2.0/24 Finance Subnet:192.168.3.0/24 Instructions: To perform the necessary tasks, please modify the DST port, Protocol, Action, and/or Rule Order columns. Firewall ACLs are read from the top down Task 1) An administrator added a rule to allow their machine terminal server access to the server subnet. This rule is not working. Identify the rule and correct this issue.
Task 2) All web servers have been changed to communicate solely over SSL. Modify the appropriate rule to allow communications.
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the network. This rule is not working. Identify and correct this issue.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.
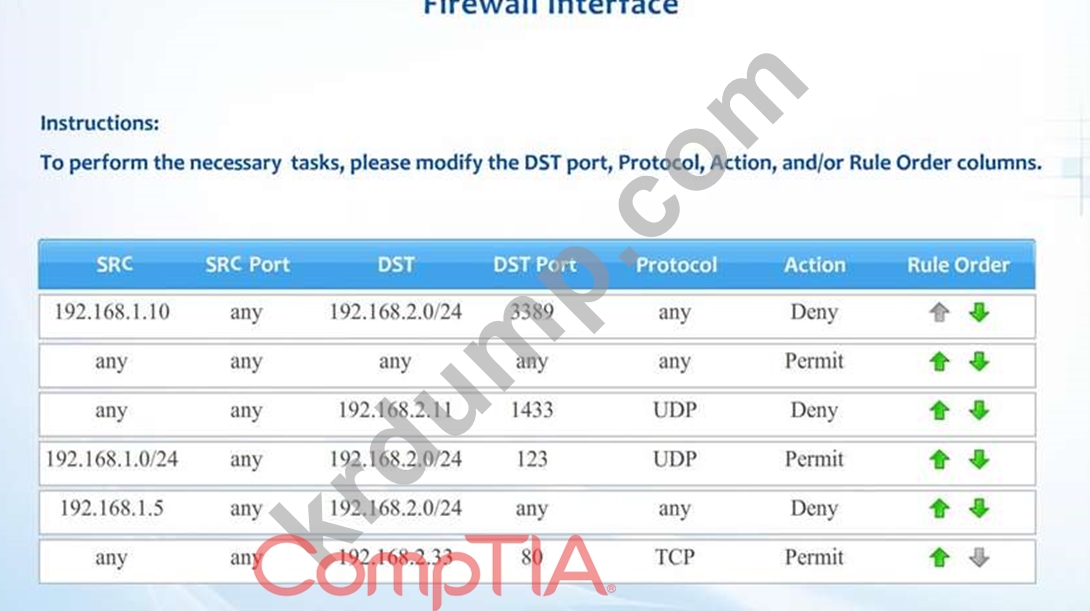
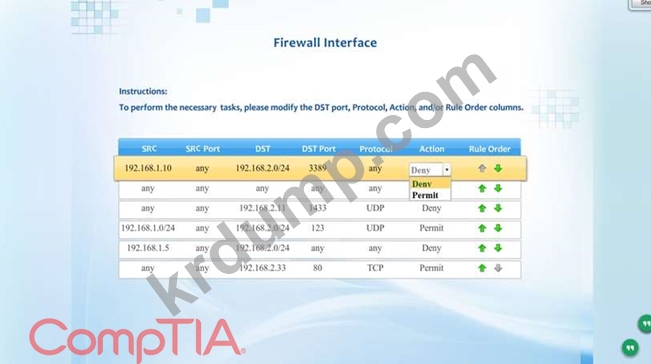
User Subnet: 192.168.1.0/24 Server Subnet: 192.168.2.0/24 Finance Subnet:192.168.3.0/24 Instructions: To perform the necessary tasks, please modify the DST port, Protocol, Action, and/or Rule Order columns. Firewall ACLs are read from the top down Task 1) An administrator added a rule to allow their machine terminal server access to the server subnet. This rule is not working. Identify the rule and correct this issue.
Task 2) All web servers have been changed to communicate solely over SSL. Modify the appropriate rule to allow communications.
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the network. This rule is not working. Identify and correct this issue.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.


CAS-003 문제 220
A security analyst is classifying data based on input from data owners and other stakeholders.
The analyst has identified three data types:
1. Financially sensitive data
2. Project data
3. Sensitive project data
The analyst proposes that the data be protected in two major groups, with further access control separating the financially sensitive data from the sensitive project data. The normal project data will be stored in a separate, less secure location. Some stakeholders are concerned about the recommended approach and insist that commingling data from different sensitive projects would leave them vulnerable to industrial espionage.
Which of the following is the BEST course of action for the analyst to recommend?
The analyst has identified three data types:
1. Financially sensitive data
2. Project data
3. Sensitive project data
The analyst proposes that the data be protected in two major groups, with further access control separating the financially sensitive data from the sensitive project data. The normal project data will be stored in a separate, less secure location. Some stakeholders are concerned about the recommended approach and insist that commingling data from different sensitive projects would leave them vulnerable to industrial espionage.
Which of the following is the BEST course of action for the analyst to recommend?

