CAS-003 문제 101
An organization has recently deployed an EDR solution across its laptops, desktops, and server infrastructure.
The organization's server infrastructure is deployed in an IaaS environment. A database within the non-production environment has been misconfigured with a routable IP and is communicating with a command and control server.
Which of the following procedures should the security responder apply to the situation? (Choose two.)
The organization's server infrastructure is deployed in an IaaS environment. A database within the non-production environment has been misconfigured with a routable IP and is communicating with a command and control server.
Which of the following procedures should the security responder apply to the situation? (Choose two.)
CAS-003 문제 102
An organization is concerned with potential data loss in the event of a disaster, and created a backup datacenter as a mitigation strategy. The current storage method is a single NAS used by all servers in both datacenters. Which of the following options increases data availability in the event of a datacenter failure?
CAS-003 문제 103
보안 테스터가 RFID 액세스 제어 시스템의 Mack-box 평가를 수행하고 있습니다. 테스터는 소수의 RFID 태그를 가지고 있어 리더기에 접근할 수 있지만 테스터는 회사에서 사용하기 때문에 리더기를 분해할 수 없습니다. 다음 중 테스터가 올바른 순서로 RFID 액세스 제어 시스템을 평가하기 위해 취해야 하는 단계를 보여 주는 것은 무엇입니까?
CAS-003 문제 104
A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company's products. The analyst believes a malicious actor is scanning the web form. To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control. Given the log below:
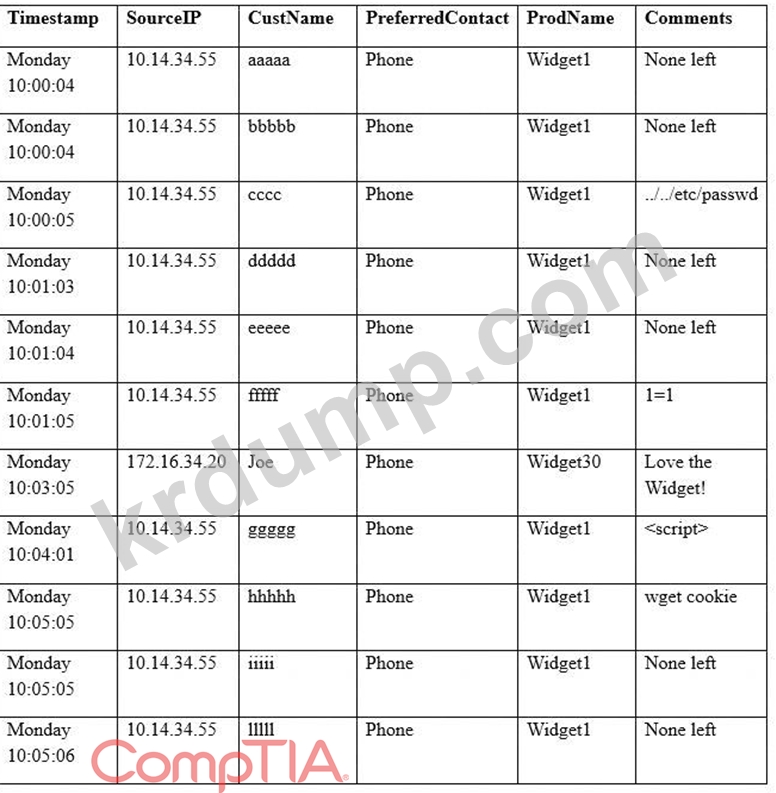
Which of the following is the MOST likely type of activity occurring?

Which of the following is the MOST likely type of activity occurring?
CAS-003 문제 105
An insurance company has two million customers and is researching the top transactions on its customer portal. It identifies that the top transaction is currently password reset. Due to users not remembering their secret questions, a large number of calls are consequently routed to the contact center for manual password resets. The business wants to develop a mobile application to improve customer engagement in the future, continue with a single factor of authentication, minimize management overhead of the solution, remove passwords, and eliminate to the contact center. Which of the following techniques would BEST meet the requirements? (Choose two.)

