1z1-116 문제 1
Examine these commands and the output used to configure Real Application Security:

What does this output mean?

What does this output mean?
1z1-116 문제 2
Which two statements are true about column-level transparent data encryption?
1z1-116 문제 3
Which three are true concerning command rules?
1z1-116 문제 4
Examine these commands that execute successfully:
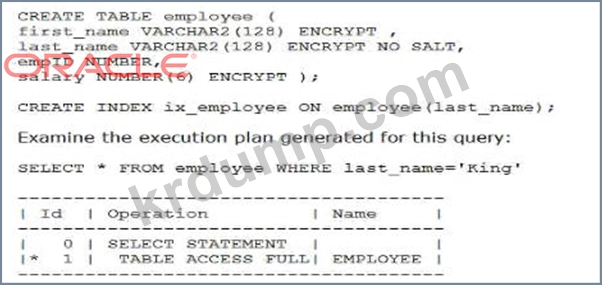
What must be done to allow the index to be used?

What must be done to allow the index to be used?
1z1-116 문제 5
What does the Application Data Modeling module of the Oracle Data Masking and Subsetting Pack search for?

