1z0-997-21 문제 46
A manufacturing company is planning to migrate their on-premises database to OCI and has hired you for the migration. Customer has provided following information regarding their existing onpremises database:
Database version, host operating system and version, database character set, storage for data staging, acceptable length of system outage.
What additional information do you need from customer in order to recommend a suitable migration method? Choose two
Database version, host operating system and version, database character set, storage for data staging, acceptable length of system outage.
What additional information do you need from customer in order to recommend a suitable migration method? Choose two
1z0-997-21 문제 47
You are part of a project team working in the development environment created in OCI. You have realized that the CIDR block specified for one of the subnet in a VCN is not correct and want to delete the subnet. While deleting you are getting an error indicating that there are still resources that you must delete first. The error includes the OCID of the VNIC that is in the subnet.
Which of the following action you will take to troubleshoot this issue?
Which of the following action you will take to troubleshoot this issue?
1z0-997-21 문제 48
You developed a microservices based application that runs on Oracle Cloud Infrastructure (OCI) Container Engine for Kubernetes (OKE). Your security team wants to use SSL termination for this application. What should you do to create a secure SSL termination for this application using fewest steps?
1z0-997-21 문제 49
You are a solutions architect for a global health care company which has numerous data centers around the globe. Due to the ever growing data that your company is storing, you were Instructed to set up a durable, cost effective solution to archive you data from your existing on-premises tape based backup Infrastructure to Oracle Cloud Infrastructure (OCI).
What is the most-effective mechanism to Implement this requirement?
What is the most-effective mechanism to Implement this requirement?
1z0-997-21 문제 50
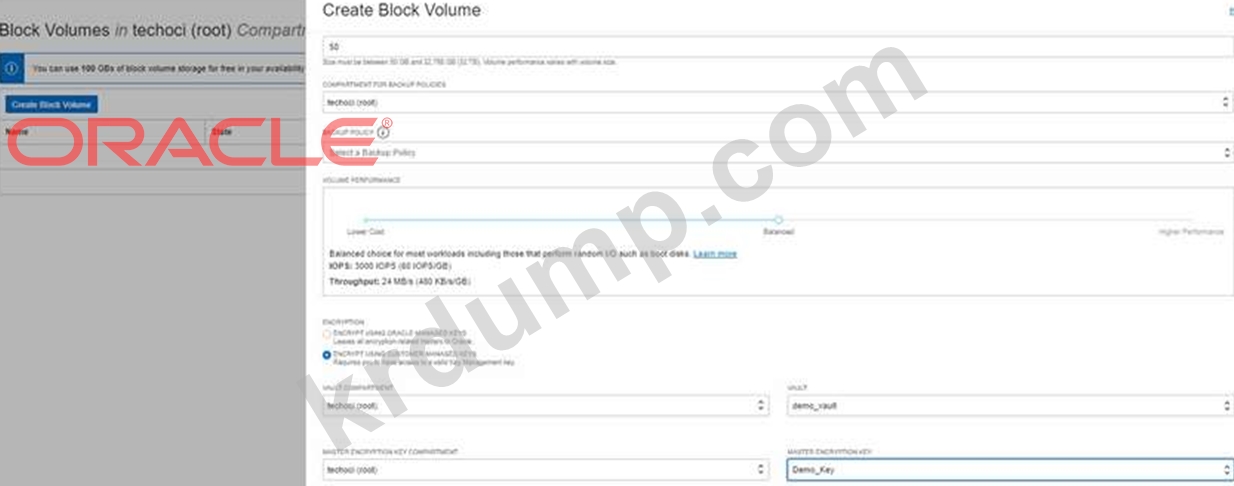
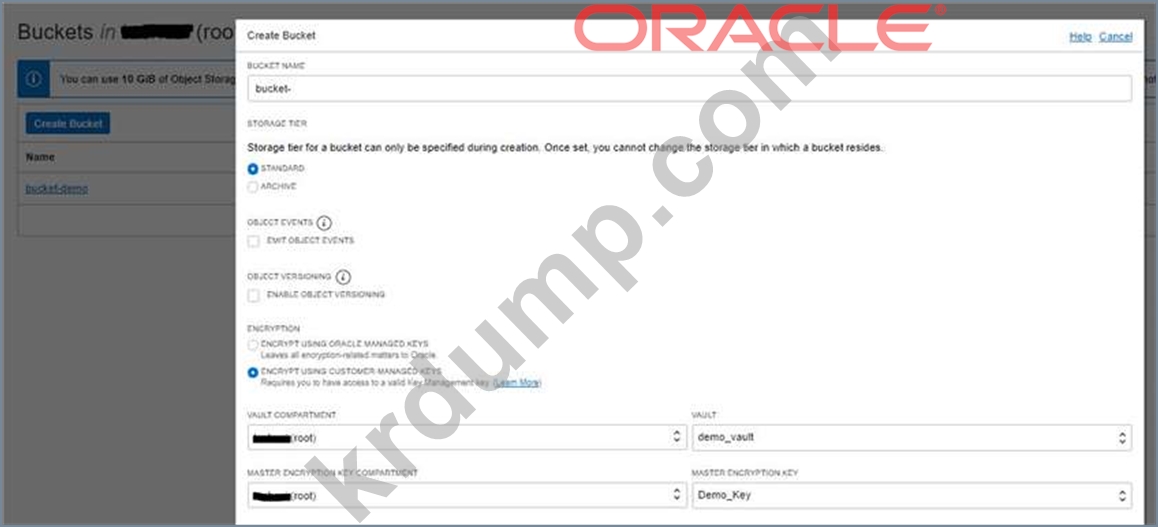
Your company will soon start moving critical systems Into Oracle Cloud Infrastructure (OCI) platform. These systems will reside in the us-phoenix-1and us-ashburn 1 regions. As part of the migration planning, you are reviewing the company's existing security policies and written guidelines for the OCI platform usage within the company. you have to work with the company managed key.
Which two options ensure compliance with this policy?
Which two options ensure compliance with this policy?