NCP-MCI-5.15 문제 16
An administrator is working with Nutanix Support and needs to provide logs for troubleshooting an issue. The cluster is located in a secure environment. Data such as IP addresses and VM names cannot be shared.
Which method should be used to anonymize the log data sent to Nutanix Support?
A)

B)
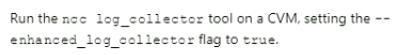
C)

D)

Which method should be used to anonymize the log data sent to Nutanix Support?
A)

B)

C)

D)

NCP-MCI-5.15 문제 17
An administrator has a 5-node cluster configured for RF2 with 200 TB of raw disk space. The administrator decides to enable Erasure Coding to gain additional usable space.
Approximately how much usable space would be available after enabling Erasure Coding?
Approximately how much usable space would be available after enabling Erasure Coding?
NCP-MCI-5.15 문제 18
In which two scenarios is Nutanix Key Management Server supported?
NCP-MCI-5.15 문제 19
A catastrophic failure occurs at the primary data center. A protection domain has been set up. All required data has been replicated to an offsite DR location.
Which button should an administrator click on at the remote site's protection domain to bring up the replicated VMs?
Which button should an administrator click on at the remote site's protection domain to bring up the replicated VMs?
NCP-MCI-5.15 문제 20
The Stargate service becomes unavailable on a single CVM on an AHV node. What is used to maintain I/O operations in the cluster?

