MS-100 문제 166
You have a Microsoft 365 subscription that uses a default named contoso.com.
Three files were created on February 1, 2019, as shown in the following table.

On March 1, 2019, you create two retention labels named Label1 and label2.
The settings for Label1 are configured as shown in the Label1 exhibit. (Click theLabel1tab.) Label 1

The settings for Label2 are configured as shown in the Label1 exhibit. (Click theLabel2tab.) Label 2

You apply the retention labels to Exchange email, SharePoint sites, and OneDrive accounts.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE:Each correct selection is worth one point.

Three files were created on February 1, 2019, as shown in the following table.

On March 1, 2019, you create two retention labels named Label1 and label2.
The settings for Label1 are configured as shown in the Label1 exhibit. (Click theLabel1tab.) Label 1

The settings for Label2 are configured as shown in the Label1 exhibit. (Click theLabel2tab.) Label 2

You apply the retention labels to Exchange email, SharePoint sites, and OneDrive accounts.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE:Each correct selection is worth one point.

MS-100 문제 167
Your network contains an on-premises Active Directory forest.
You are evaluating the implementation of Microsoft 365 and the deployment of an authentication strategy.
You need to recommend an authentication strategy that meets the following requirements:
* Allows users to sign in by using smart card-based certificates
* Allows users to connect to on-premises and Microsoft 365 services by using SSO Which authentication strategy should you recommend?
You are evaluating the implementation of Microsoft 365 and the deployment of an authentication strategy.
You need to recommend an authentication strategy that meets the following requirements:
* Allows users to sign in by using smart card-based certificates
* Allows users to connect to on-premises and Microsoft 365 services by using SSO Which authentication strategy should you recommend?
MS-100 문제 168
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities. The solution must meet the following requirements:
Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
Users passwords must be 10 characters or more.
Solution: Implement password hash synchronization and modify the password settings from the Default Domain Policy in Active Directory.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities. The solution must meet the following requirements:
Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
Users passwords must be 10 characters or more.
Solution: Implement password hash synchronization and modify the password settings from the Default Domain Policy in Active Directory.
Does this meet the goal?
MS-100 문제 169
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities. The solution must meet the following requirements:
* Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
* Users passwords must be 10 characters or more.
Solution: Implement password hash synchronization and configure password protection in the Azure AD tenant.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities. The solution must meet the following requirements:
* Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
* Users passwords must be 10 characters or more.
Solution: Implement password hash synchronization and configure password protection in the Azure AD tenant.
Does this meet the goal?
MS-100 문제 170
Your company is based in the United Kingdom (UK).
Users frequently handle data that contains Personally Identifiable Information (PII).
You create a data loss prevention (DLP) policy that applies to users inside and outside the company. The policy is configured as shown in the following exhibit.
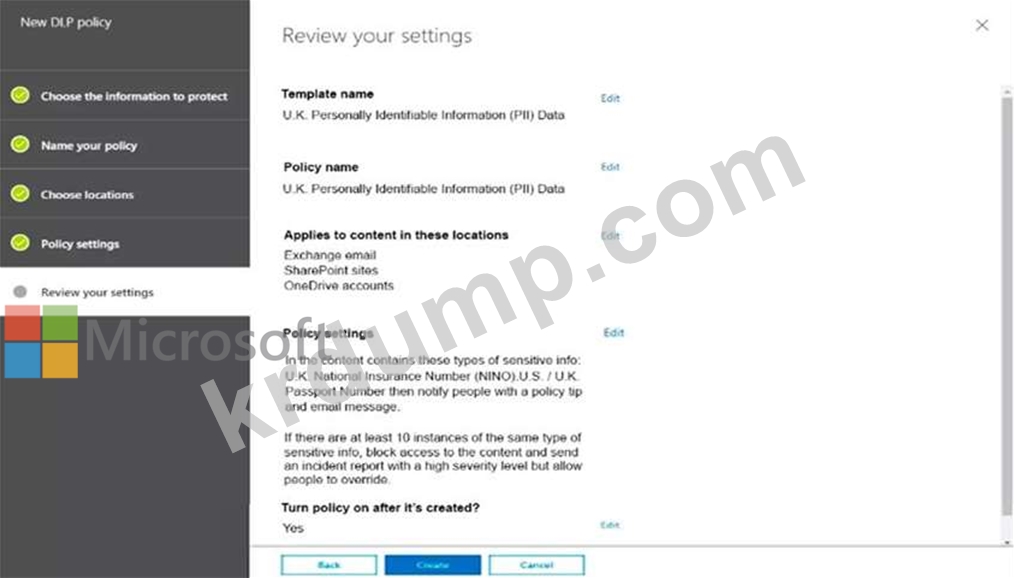
Use the drop-down menus to select the answer choice that completes each statement based in the information presented in the information presented in the graphic.
NOTE: Each correct selection is worth one point.
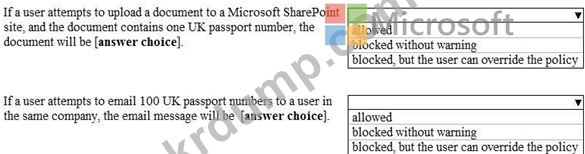
Users frequently handle data that contains Personally Identifiable Information (PII).
You create a data loss prevention (DLP) policy that applies to users inside and outside the company. The policy is configured as shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based in the information presented in the information presented in the graphic.
NOTE: Each correct selection is worth one point.

프리미엄 번들
DumpTop 에서 공유하는 최신 MS-100 시험 덤프는 MS-100 시험패스를 도와드릴수 있습니다! DumpTop 은 최근 업데이트된 MS-100 시험자료를 제공해드립니다. DumpTop MS-100 덤프도 시험문제 변경에 따라 업데이트되었으며 오답도 수정되었습니다. DumpTop MS-100 덤프 최신버전을 공유받아보세요.
(431 Q&As 덤프, 30%OFF할인코드: KrDump)