AZ-304 문제 141
You have an Azure Active Directory (Azure AD) tenant and Windows 10 devices.
You configure a conditional access policy as shown in the exhibit. (Click the Exhibit tab.)
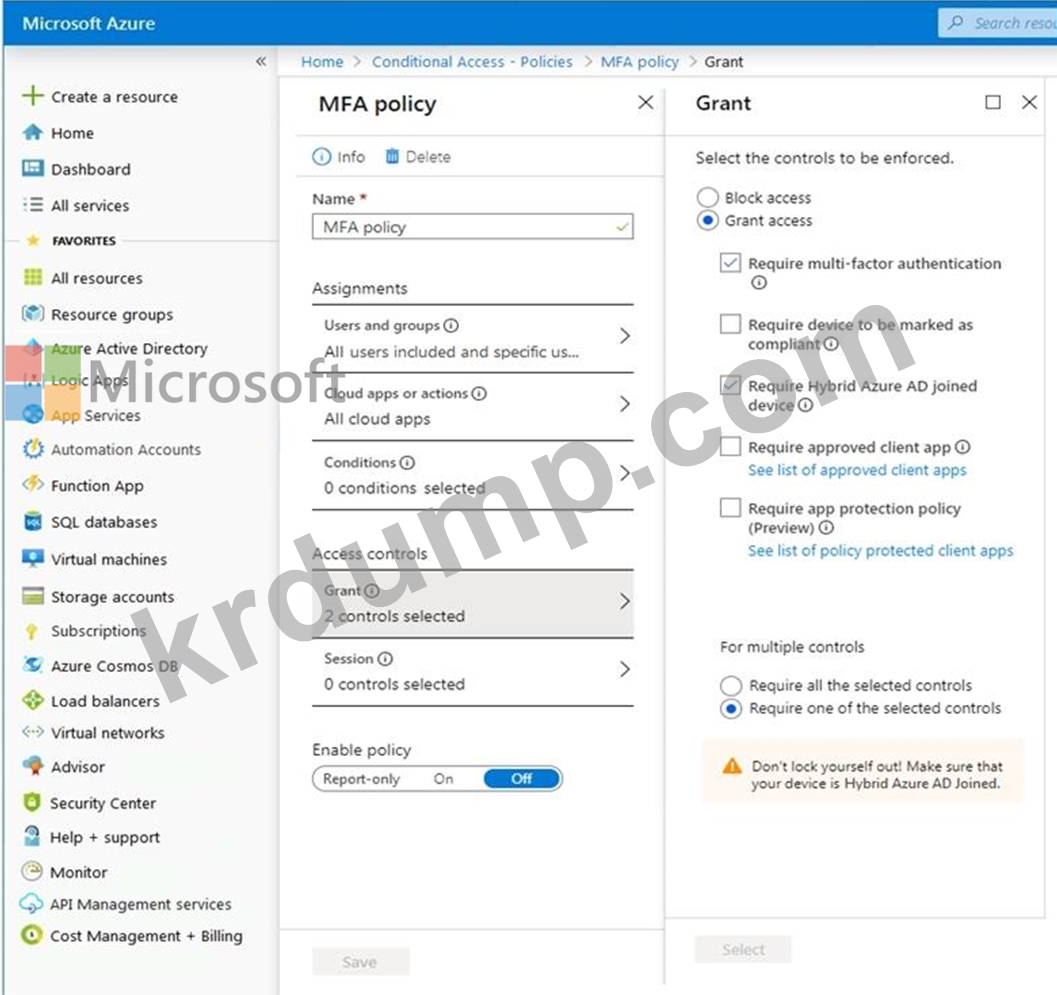
What is the result of the policy?
You configure a conditional access policy as shown in the exhibit. (Click the Exhibit tab.)

What is the result of the policy?
AZ-304 문제 142
You need to recommend a strategy for the web tier of WebApp1. The solution must minimize What should you recommend?
AZ-304 문제 143
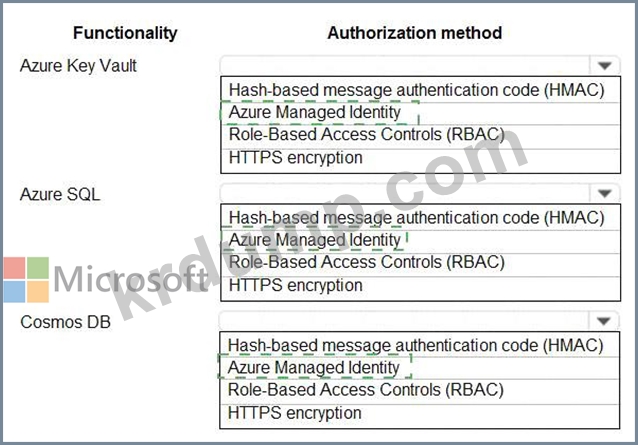
You are building an application that will run in a virtual machine (VM). The application will use Azure Managed Identity.
The application uses Azure Key Vault, Azure SQL Database, and Azure Cosmos DB.
You need to ensure the application can use secure credentials to access these services.
Which authentication method should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
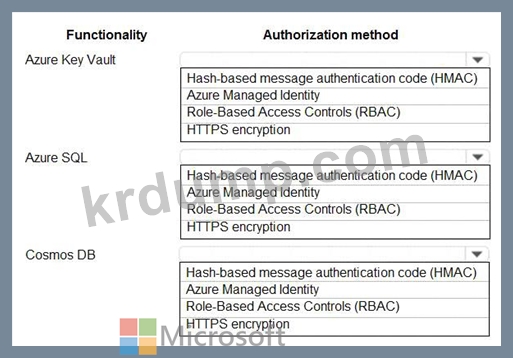
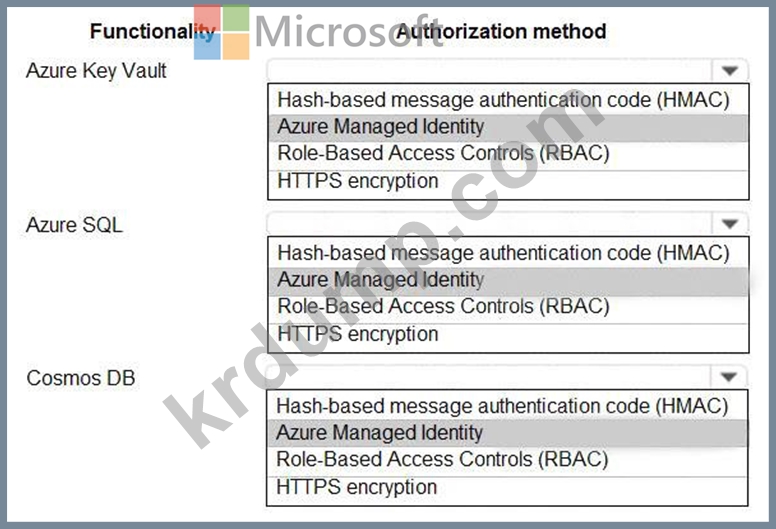
The application uses Azure Key Vault, Azure SQL Database, and Azure Cosmos DB.
You need to ensure the application can use secure credentials to access these services.
Which authentication method should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-304 문제 144
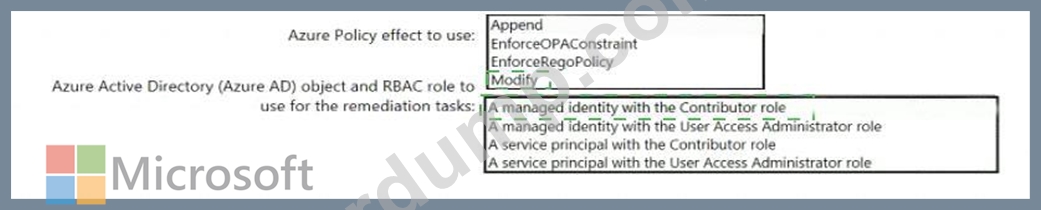
You need to design an Azure policy that will implement the following functionality:
* For new resources, assign tags and values that match the tags and values of the resource group to which the resources are deployed.
* For existing resources, identify whether the tags and values match the tags and values of the resource group that contains the resources.
* For any non-compliant resources, trigger auto-generated remediation tasks to create missing tags and values.
The solution must use the principle of least privilege.
What should you include in the design? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
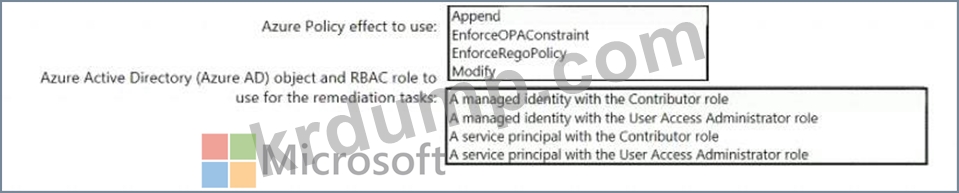
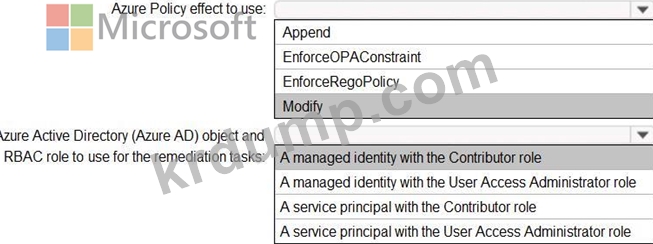
* For new resources, assign tags and values that match the tags and values of the resource group to which the resources are deployed.
* For existing resources, identify whether the tags and values match the tags and values of the resource group that contains the resources.
* For any non-compliant resources, trigger auto-generated remediation tasks to create missing tags and values.
The solution must use the principle of least privilege.
What should you include in the design? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-304 문제 145
Your company, named Contoso, Ltd, implements several Azure logic apps that have HTTP triggers: The logic apps provide access to an on-premises web service.
Contoso establishes a partnership with another company named Fabrikam, Inc.
Fabrikam does not have an existing Azure Active Directory (Azure AD) tenant and uses third-party OAuth 2.0 identity management to authenticate its users.
Developers at Fabrikam plan to use a subset of the logics apps to build applications that will integrate with the on-premises web service of Contoso.
You need to design a solution to provide the Fabrikam developers with access to the logic apps. The solution must meet the following requirements:
* Requests to the logic apps from the developers must be limited to lower rates than the requests from the users at Contoso.
* The developers must be able to rely on their existing OAuth 2.0 provider to gain access to the logic apps.
* The solution must NOT require changes to the logic apps.
* The solution must NOT use Azure AD guest accounts.
What should you include in the solution?
Contoso establishes a partnership with another company named Fabrikam, Inc.
Fabrikam does not have an existing Azure Active Directory (Azure AD) tenant and uses third-party OAuth 2.0 identity management to authenticate its users.
Developers at Fabrikam plan to use a subset of the logics apps to build applications that will integrate with the on-premises web service of Contoso.
You need to design a solution to provide the Fabrikam developers with access to the logic apps. The solution must meet the following requirements:
* Requests to the logic apps from the developers must be limited to lower rates than the requests from the users at Contoso.
* The developers must be able to rely on their existing OAuth 2.0 provider to gain access to the logic apps.
* The solution must NOT require changes to the logic apps.
* The solution must NOT use Azure AD guest accounts.
What should you include in the solution?
프리미엄 번들
DumpTop 에서 공유하는 최신 AZ-304 시험 덤프는 AZ-304 시험패스를 도와드릴수 있습니다! DumpTop 은 최근 업데이트된 AZ-304 시험자료를 제공해드립니다. DumpTop AZ-304 덤프도 시험문제 변경에 따라 업데이트되었으며 오답도 수정되었습니다. DumpTop AZ-304 덤프 최신버전을 공유받아보세요.
(288 Q&As 덤프, 30%OFF할인코드: KrDump)