AZ-304 문제 66
You plan to deploy 10 applications to Azure. The applications will be deployed to two Azure Kubermetes Service (AKS) clusters. Each cluster win be deployed to a separate Azure region. The application deployment must meet the following requirements:
* Ensure that the applications remain available it a single AKS cluster fails.
* Ensure That the connection traffic over the internet is encrypted by using SSL without having to configure SSL on each container.
Which Azure service should you include in the recommendation?
* Ensure that the applications remain available it a single AKS cluster fails.
* Ensure That the connection traffic over the internet is encrypted by using SSL without having to configure SSL on each container.
Which Azure service should you include in the recommendation?
AZ-304 문제 67
Your company has the offices shown in the following table.
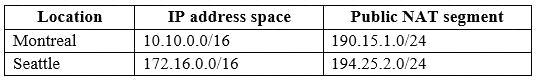
The network contains an Active Directory domain named contoso.com that is synced to Azure Active Directory (Azure AD).
All users connect to an application hosted in Microsoft 365.
You need to recommend a solution to ensure that all the users use Azure Multi-Factor Authentication (MFA) to connect to the application from one of the offices.
What should you include in the recommendation?

The network contains an Active Directory domain named contoso.com that is synced to Azure Active Directory (Azure AD).
All users connect to an application hosted in Microsoft 365.
You need to recommend a solution to ensure that all the users use Azure Multi-Factor Authentication (MFA) to connect to the application from one of the offices.
What should you include in the recommendation?
AZ-304 문제 68
You have an on-premises Hyper-V cluster that hosts 20 virtual machines. Some virtual machines run Windows Sever 2016 and some run Linux.
You plan to mitigate the virtual machines to an Azure subscription.
You need to recommend a solution to replicate the disks of the virtual machines to Azure. The solution must ensure that the virtual machines remain available during the migration of the disks.
Solution: You recommend implement an Azure Storage account, and then using Azure Migrate.
You plan to mitigate the virtual machines to an Azure subscription.
You need to recommend a solution to replicate the disks of the virtual machines to Azure. The solution must ensure that the virtual machines remain available during the migration of the disks.
Solution: You recommend implement an Azure Storage account, and then using Azure Migrate.
AZ-304 문제 69
A company has a hybrid ASP.NET Web API application that is based on a software as a service (SaaS) offering.
Users report general issues with the data. You advise the company to implement live monitoring and use ad hoc queries on stored JSON data. You also advise the company to set up smart alerting to detect anomalies in the data.
You need to recommend a solution to set up smart alerting.
What should you recommend?
Users report general issues with the data. You advise the company to implement live monitoring and use ad hoc queries on stored JSON data. You also advise the company to set up smart alerting to detect anomalies in the data.
You need to recommend a solution to set up smart alerting.
What should you recommend?
AZ-304 문제 70
You have 200 resource groups across 20 Azure subscriptions.
Your company's security policy states that the security administrator must verify all assignments of the Owner role for the subscriptions and resource groups once a month. All assignments that are not approved by the security administrator must be removed automatically. The security administrator must be prompted every month to perform the verification.
What should you use to implement the security policy?
Your company's security policy states that the security administrator must verify all assignments of the Owner role for the subscriptions and resource groups once a month. All assignments that are not approved by the security administrator must be removed automatically. The security administrator must be prompted every month to perform the verification.
What should you use to implement the security policy?

