CAS-003 문제 356
보안 관리자가 IPS-IDS 시스템에서 모니터링하는 특정 포트 및 IP 주소와 회사와 새 비즈니스 파트너 간의 경계 네트워크에 대한 방화벽 배치를 확인하고 있습니다. 다음 비즈니스 문서 중 보안 관리자가 수행해야 하는 매개변수를 정의하는 문서 확인하다?
CAS-003 문제 357
A security administrator at Company XYZ is trying to develop a body of knowledge to enable heuristic and behavior based security event monitoring of activities on a geographically distributed network. Instrumentation is chosen to allow for monitoring and measuring the network.
Which of the following is the BEST methodology to use in establishing this baseline?
Which of the following is the BEST methodology to use in establishing this baseline?
CAS-003 문제 358
A Chief Information Securiy Officer (CISO) is reviewing technical documentation from various regional offices and notices some key differences between these groups. The CISO has not discovered any governance documentation. The CISO creates the following chart to visualize the differences among the networking used.
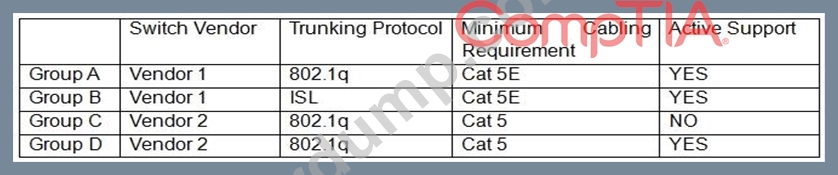
Which of the following would be the CISO's MOST immediate concern?

Which of the following would be the CISO's MOST immediate concern?
CAS-003 문제 359
An e-commerce company that provides payment gateways is concerned about the growing expense and time associated with PCI audits of its payment gateways and external audits by customers for their own compliance reasons The Chief Information Officer (CIO) asks the security team to provide a list of options that will:
1. Reduce the overall cost of these audits
2. Leverage existing infrastructure where possible
3. Keep infrastructure costs to a minimum
4. Provide some level of attestation of compliance
Which of the following will BEST address the CIO"s concerns? (Select TWO)
1. Reduce the overall cost of these audits
2. Leverage existing infrastructure where possible
3. Keep infrastructure costs to a minimum
4. Provide some level of attestation of compliance
Which of the following will BEST address the CIO"s concerns? (Select TWO)
CAS-003 문제 360
Joe an application security engineer is performing an audit of an environmental control application He has implemented a robust SDLC process and is reviewing API calls available to the application During the review.
Joe finds the following in a log file.
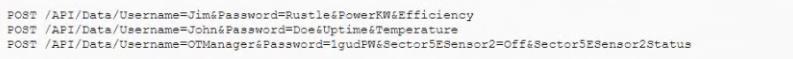
Which of the following would BEST mitigate the issue Joe has found?
Joe finds the following in a log file.

Which of the following would BEST mitigate the issue Joe has found?

