CAS-003 문제 286
An infrastructure team is at the end of a procurement process and has selected a vendor. As part of the
final negotiations, there are a number of outstanding issues, including:
1. Indemnity clauses have identified the maximum liability
2. The data will be hosted and managed outside of the company's geographical location
The number of users accessing the system will be small, and no sensitive data will be hosted in the
solution. As the security consultant on the project, which of the following should the project's security
consultant recommend as the NEXT step?
final negotiations, there are a number of outstanding issues, including:
1. Indemnity clauses have identified the maximum liability
2. The data will be hosted and managed outside of the company's geographical location
The number of users accessing the system will be small, and no sensitive data will be hosted in the
solution. As the security consultant on the project, which of the following should the project's security
consultant recommend as the NEXT step?
CAS-003 문제 287
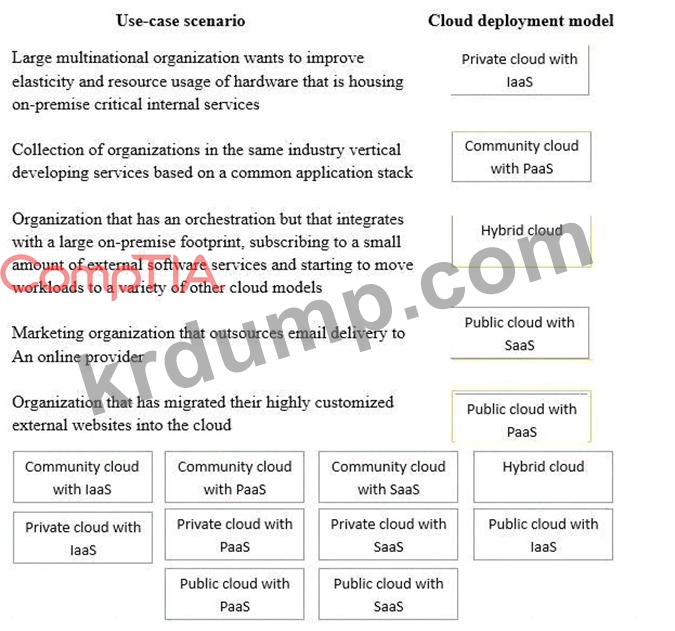
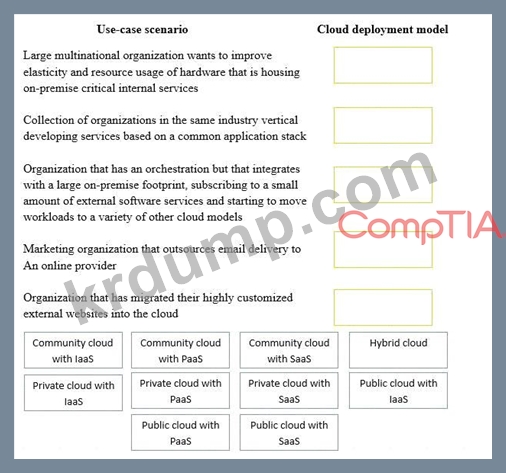
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.

CAS-003 문제 288
ABC Corporation has introduced token-based authentication to system administrators due to the risk of password compromise. The tokens have a set of HMAC counter-based codes and are valid until they are used.
Which of the following types of authentication mechanisms does this statement describe?
Which of the following types of authentication mechanisms does this statement describe?
CAS-003 문제 289
A security engineer has been hired to design a device that will enable the exfiltration of data from within a well- defended network perimeter during an authorized test. The device must bypass all firewalls and NIDS in place, as well as allow for the upload of commands from a centralized command and control server . The total cost of the device must be kept to a minimum in case the device is discovered during an assessment.
Which of the following tools should the engineer load onto the device being designed?
Which of the following tools should the engineer load onto the device being designed?
CAS-003 문제 290
A security engineer is working on a large software development project. As part of the design of the project, various stakeholder requirements were gathered and decomposed to an implementable and testable level.
Various security requirements were also documented.
Organize the following security requirements into the correct hierarchy required for an SRTM.
Requirement 1: The system shall provide confidentiality for data in transit and data at rest.
Requirement 2: The system shall use SSL, SSH, or SCP for all data transport.
Requirement 3: The system shall implement a file-level encryption scheme.
Requirement 4: The system shall provide integrity for all data at rest.
Requirement 5: The system shall perform CRC checks on all files.
Various security requirements were also documented.
Organize the following security requirements into the correct hierarchy required for an SRTM.
Requirement 1: The system shall provide confidentiality for data in transit and data at rest.
Requirement 2: The system shall use SSL, SSH, or SCP for all data transport.
Requirement 3: The system shall implement a file-level encryption scheme.
Requirement 4: The system shall provide integrity for all data at rest.
Requirement 5: The system shall perform CRC checks on all files.